Security Tips
We understand that information security is of utmost importance to you when it comes to establishing remote desktop connections. We apply industry-standard security technologies to protect your data and comply with the strictest security standards.
To establish a remote desktop support connection with a client, the helpdesk operator needs to start the ISL Light application which carries an RSA 2048/4096-bit Public Key of the ISL Online server. ISL Online secures its standard remote desktop connection by using AES 256-bit end-to-end encryption. STUN/TURN servers enable a direct connection, while signaling and control channel remain on ISL Online servers. In such cases, ECDSA P-256 manages encryption key negotiation using the Diffie-Hellman key exchange algorithm, securing the connection using AES 256-bit end-to-end encryption.
The software supports two-factor authentication, exportable audit logs, automatic session recording and external authentication.
For a more detailed overview please read our security statement.
Below we want to give you a quick insight into some of the most important features ISL Online provides to guarantee secure use of remote desktop software.
Login
When you log into your account or ISL Light, we recommend using a strong password and setting two-factor authentication to make your account more secure.
Use strong account password
The security of your data depends not only on the strength of the encryption method but also on the strength of your password.
To help you create a strong password, ISL Online's password security policy is based on the latest NIST specifications. Your password must be at least 8 characters long. You are allowed to use any printable ASCII characters and spaces, while any leading and trailing spaces will be removed. Your password is checked against the deny list, which consists of the most common and simple passwords.
Set two-factor authentication
Two-factor authentication (2FA) is an extra layer of security for help desk technicians and IT professionals. With 2FA enabled, operators can only log in to the ISL Online system by going through a two-step verification process by providing something they know (password) and something they have (2FA token).
How to set up two-factor authentication
Important: We recommend setting more than one two-factor authentication method, such as mobile and email. This gives you a backup option to log in, in case you lose access to one method.
External authentication (server license only)
Various types of authentication schemes can be integrated into the ISL Online system, such as OpenLDAP, Microsoft Active Directory, Novell eDirectory, or RADIUS. When external authentication is configured, operator access rights and permissions to use the ISL Online software are managed by IT administrators using their corporate user management directories.
Access Password
When you install unattended access (ISL AlwaysOn) on a remote computer, you must set a secure access password. This will be your main access password, which you must provide each time you try to access the remote computer.
Main Access Password
Main access password is an access password which is defined during installation, and can be used to connect to the remote computer by any user.
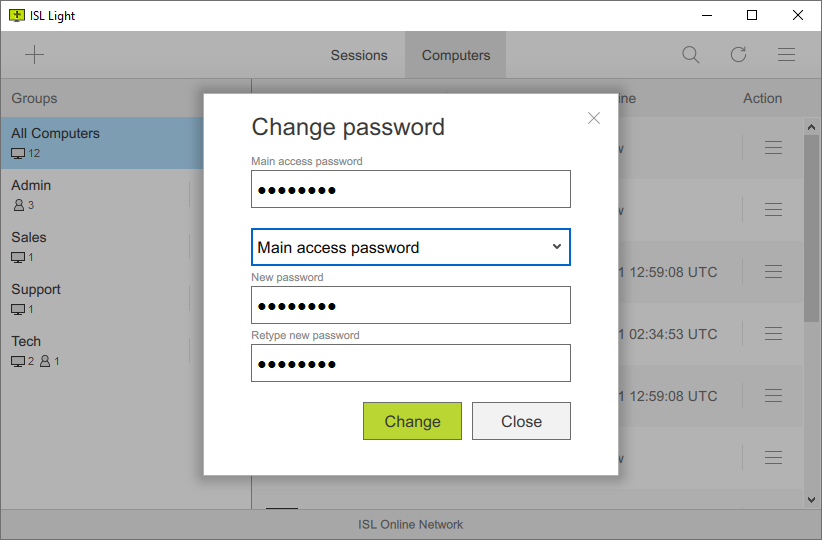
Connection Access Password
If you have shared access to a remote computer with other users in your account, you have the ability to set a different password for each user. Connection access password can be set manually in the ISL AlwaysOn settings.
One-Time Password
Generate one-time passwords manually in the ISL AlwaysOn settings. Each one-time password can only be used once to connect to a remote computer.
Read manual Watch video (3:14)
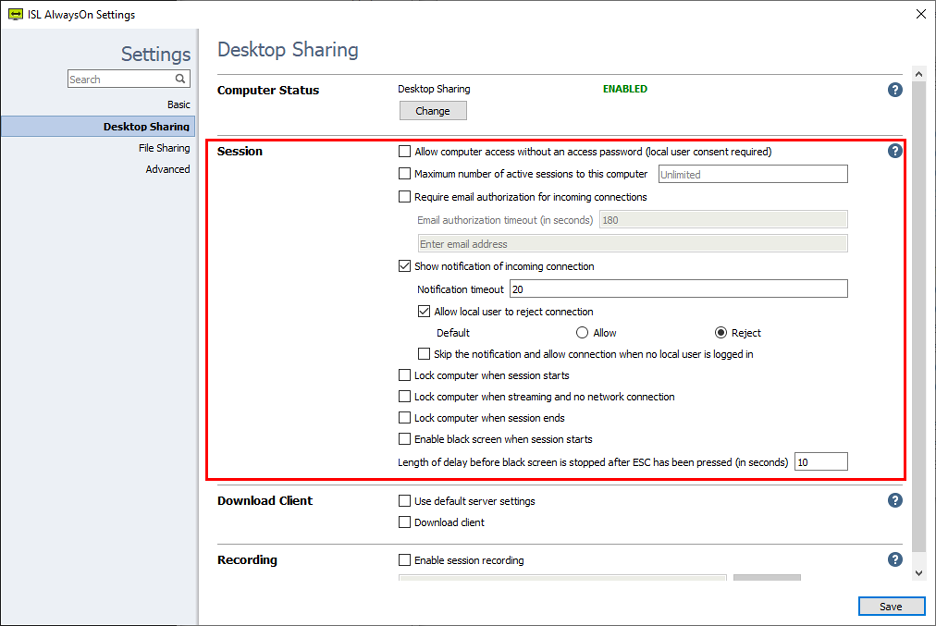
Additional Settings
The ISL AlwaysOn settings allow you to modify or customise several security settings for connecting to an unattended computer.
Allow computer access also with local user consent and no access password
Allows the operator to connect to a remote computer without an access password. In this case, the local user has to approve the connection. To use this setting you have to use the next command line parameters when starting ISL Light:
ISLLight.exe --username "<isl_online_username>" --password "<password>" --connect-search "<computer_description>/<computer_name>" --consent-message "<message to be displayed>"
Maximum number of active sessions to this computer
Allows to set the maximum number of active sessions to this computer. For example, to limit the access to one simultaneous connection to the computer use value "1". The default is set to Unlimited.
Show Notification of incoming connection
Allows the client to see a countdown notification when a connection is being established to their computer. You can specify the timeout and the options available to the local user. After timeout the default action is executed if the remote user is allowed to reject connection.
Allow local user to reject connection
This option becomes available if you have enabled the "Show notification of incoming connection" option. The local user sees a notification that gives them the option to accept or reject the connection made by the supporter.
Lock computer when session starts
Lock the remote computer when the session starts, you will have to enter the account info to log in.
Lock computer when streaming and no network connection
If the connection is interrupted while connected to the remote computer, the remote computer is automatically locked.
Lock computer when session ends
Automatically lock the remote computer when session ends.
Enable black screen when session starts
The local user will see a black screen when the remote session is active.
Length of delay before black screen is stopped after ESC has been pressed (in seconds)
Set the timeout in seconds that starts when you press ESC. Once timed out, the black screen is disabled and the local client can see the screen. The maximum timeout is 180 seconds.
Email Notifications
Receive an email notification each time a remote access session starts, stops, fails or a file is downloaded on a specific computer.
Read manual Watch video (0:58)
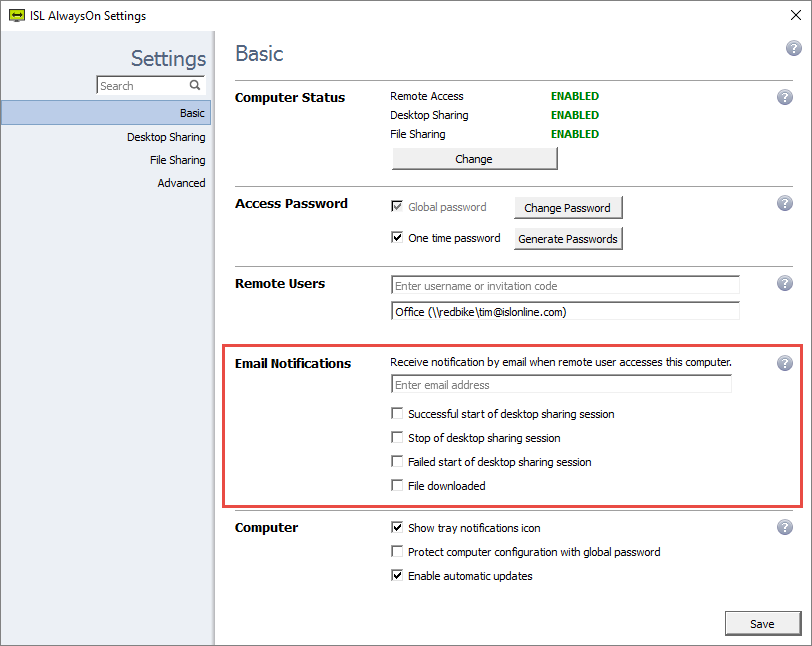
Access Filters
For security reasons you might want to restrict the use of ISL Online software within your organisation. You are able to limit the data access to ISL Online servers based on the IP and/or MAC addresses. You can use the “allow” function to specify lists of IP/MAC addresses that are allowed to start a remote support session or access an unattended computer. On the other hand, you can use the “deny” function to specify the lists of IP/MAC addresses. These rules can be defined for a specific user or the entire domain on the ISL Online server.
For example, you can allow your employees to generate session codes for a remote support session from the office only (your company‘s range of IP addresses).
- deny_ip 192.168.0.14
- allow_ip 192.168.0.13/255.255.255.0
- allow_mac 00-19-d1-06-c9
IP and MAC addresses can be spoofed, so filters alone are not a substitute for a strong access password!
Read manual Watch video (0:56)
Port Filtering
Good remote desktop software works without making any firewall adjustments.
With ISL Online, your firewall can remain intact as ISL Light automatically initiates an outgoing connection, trying to connect using ports 7615, 80 or 443.
However, larger organisations may have a policy in place regarding the configuration of their firewalls or proxies. System administrators might want to open port 7615 only to pass the ISL Online traffic through directly and keep filtering the rest. They can also configure DNS name exception or IP address exception.
Regardless of the network configuration, ISL Online apps will automatically try different approaches to find a working transport (detecting proxy settings, using WinINet, creating a tunnel, making use of the wildcard DNS etc.). When a Direct Connection is used, the firewall must allow connection via the ports needed for STUN and TURN protocols. Most commonly port 3478 is used, however relay connections are made on arbitrary high ports.
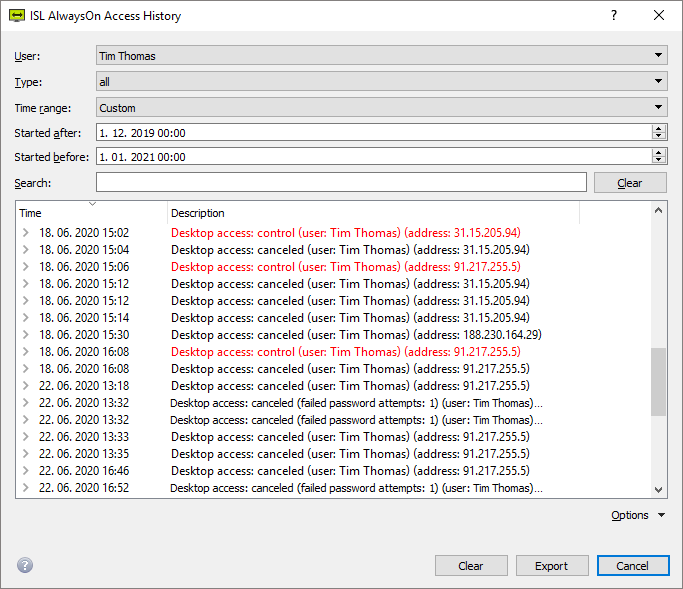
Computer Access History
Search connections that have been established within your account, desktop connection timestamps, and other useful information.
Read manual Watch video (0:34)
Restriction on Features
Remote desktop software is a universal tool, used virtually in all industries. Accordingly, there are countless different use cases which call for very flexible solutions that allow restriction on features to adhere to distinct security standards.
ISL Online allows you to restrict features that are available within a session: taking control of the remote computer, transferring files between customer and operator and many other features.
An example of where restricting a feature is essential: a bank employee should be able to see a client's computer screen, but should never be able to start sharing his/her own desktop. In this case, desktop sharing on the desk side can be disabled.
Intranet (LAN-only) Option
Some large organisations only use ISL Online for their internal support across different geographical locations. In such cases remote desktop software must allow establishing remote desktop sessions within a local area network (LAN) only.
If you plan to use ISL Online within your LAN (intranet) only, there is no need for a public IP address. You only need a private address in the range of private networks (as specified in RFC 1918).
Top Questions
-
What ports need to be open for hosted solution?
Port 7615 is the preferred choice and you can think of it as the standard ISL Online port, just like 22 is ssh, 23 telnet, 25 smtp, 3389 rdp etc. - you can also find it in the list of ports at wikipedia.
Having a specific port is also very convenient - if you have a certain company policy and use a firewall/proxy, but would like to adjust it to allow ISL Online traffic, we simply instruct you to open port 7615 and all ISL Online products will work great. If we only used 80/443, the admin would find it difficult to try and allow ISL Online but limit other traffic that also goes through port 80/443.
In general, the first thing to consider when dealing with a proxy environment is to check with the system/network administrator if it is possible to make an exception. This does not mean that you completely disable the proxy, just let the ISL Online traffic through directly and keep filtering the rest. If the proxy supports DNS name exceptions, then allow direct outgoing tcp connection for port 7615 to *.islonline.net. If the proxy only supports only IP number exceptions, check this link for a current list of our server IPs. Direct connection offers best performance and minimum delays.
In an ideal world of direct connections and flexible security policies, the story would end here, but since there are many customers behind corporate firewalls/proxies where only http and https traffic is allowed (so, port 80 and/or 443) and system/network administrators do not want or are not allowed to add exceptions, we also support that and our applications try to find a working transport even in those situations (detect proxy settings, use wininet, create a tunnel, make use of the wildcard dns - helps with some proxies, etc.).
Situations where such filtering is involved can suffer from additional delays, mainly due to transport timeouts in the connection establishment process. ISL Online products always (well, unless you force a certain transport type through registry or command line) try direct connection using port 7615 and if that fails, they try ports 80 and 443 with various proxy methods. Each transport type has a timeout of 7 seconds and on windows we try 8 transport types, so if it is the last one that gets through, this means almost 1 minute delay. If a customer complains about long delays, the best thing to do is connect to the problematic computer and click find best transport in our utility connection tester. It will show you a list of successful transports along with the average transfer rate, delays etc. These results will allow you to force the best transport. Both you and your customer will appreciate the reduced connection delay.
If you need help when dealing with ISL Online products in proxy environments, you can contact ISL Online team over the telephone, via e-mail or through our live chat.
-
How long does the system keep an ISL Light session?
A session is active while ISL Light is active. When ISL Light is closed or only the session is closed by pressing "End Session" button, the session is not active any more. The system keeps the basic session info (ISL Light and Client computers' IP numbers, chat transcript, amount of transferred data etc.). The session can also be automatically terminated after specified user idle time (link). Idle time counts as time from the last user action on the computer.
-
How should I configure my firewall for optimal ISL Online experience?
If you do not filter outgoing connections, then you do not need to make any changes. However, if you do filter outgoing connections, please whitelist all connections to *.islonline.net, if your firewall allows DNS whitelisting. If you can only whitelist IP addresses, check the next question.
-
How should I configure my firewall for optimal ISL Online experience if my firewall does not support DNS allowlisting? Which IP addresses should I allow?
Please refer to list of servers for an up-to-date list of our server IP addresses. However, please keep in mind that the list of our servers changes over time (new servers are added, old servers are decomissioned), so you should check the provided link every now and then and update your firewall appropriately. Instead, intermediary ISL Online forward proxy can be configured to minimize the list of rules and keep its maintenance at lowest. For additional information, please refer to the manual.
-
How secure is your ISL Light software to prevent "hackers" from accessing my computer while using your software?
ISL Light uses industry standard SSL/TLS encryption. You can be sure that your session is private - it is encrypted end-to-end - from ISL Light Client to ISL Light. The client also has to allow each action, so the operate cannot just take over your computer. You do not need to change anything in your Operating System settings. For additional information, please refer to the security.
-
Does the session continue if my local IP changes in the middle of the session?
Yes, ISL Light reconnects back to the server, it's almost the same as if you unplugged the cable and plugged it back in.
Continue Reading: More About Security