ISL Online Glossary
Here's a glossary explaining some of the terms commonly used in ISL Online software.
Basic
ISL Online
ISL Online is a remote desktop software solution developed by ISL Remote d.o.o., a private limited company based in Ljubljana, Slovenia. ISL Online provides a remote desktop software solution that allows users to remotely access and control computer and mobile devices over the internet for business purposes. The software is available as both cloud-based and on-premises deployments, offering businesses flexibility in choosing the solution that best meets their needs.
ISL Online is used by a wide range of businesses around the world, including IT support teams, customer service departments, and sales teams. The software provides a variety of features, including remote access, file transfer, chat, session recording, and two-factor authentication, to name a few.
ISL Light is a software module that enables users (operators) to establish a connection with a remote computer or mobile device, view a remote screen, and control a remote device.
ISL Light provides users with a variety of features, including remote access and control, file transfer, chat, session recording, and multi-monitor support, among others. The software can be used for a range of purposes, such as remote support, remote training, and remote access to office computers.
To establish a remote connection with a device, the technician can install or run once the ISL Light software on their device. Once logged in, the user can connect to a remote computer or mobile device. After the connection is established, the user can view the remote screen and control the device as if they were physically present at the location.
ISL Light is designed to be easy to use and offers a high level of security to protect the privacy and confidentiality of the remote session. The software is available on multiple platforms, including Windows, macOS, Linux, iOS, and Android.
ISL Light Client is a lightweight remote desktop software that allows end-users to join remote desktop sessions established by operators using ISL Light. The lightweight design of the ISL Light Client makes it fast and easy to use, providing end-users with a smooth and seamless desktop sharing experience.
ISL Light Client is also highly customizable, allowing businesses to personalize the appearance and functionality of the software to meet their specific needs. The software is available on multiple platforms, including Windows, macOS, Linux, iOS, and Android.
ISL AlwaysOn is a remote access agent that enables users to access their computers securely from anywhere in the world. The software provides a high level of security and reliability, enabling users to work remotely and access files and applications as if they were physically present behind their computers.
ISL AlwaysOn remote access agent needs to be installed on the local computer and properly configured to enable the user to connect to the computer from a remote location using a web browser or the ISL Light software. Once the connection is established, users can access files and applications on the remote computer.
ISL Conference Proxy is a software that runs on ISL Online's network of servers or on your own server in the case of a self-hosted solution. It allows users to connect to an ISL Online session through a proxy server. The proxy server acts as an intermediary between the user's local computer and the remote computer, enabling users to join a session even if they are behind a restrictive firewall or network.
ISL Conference Proxy also includes the following features:
- GeoIP: It can detect a user's location and redirect them to the closest available proxy server.
- Distributed sessions: It can distribute the load of a session across multiple proxy servers to ensure optimal performance.
- Load balancing: It can balance the load of multiple sessions across multiple proxy servers to ensure maximum scalability and stability.
ISL Conference Proxy allows users to connect to remote computers in accordance with the strictest security standards.
ISL Online Network
The ISL Online Network, also known as ISL Online Cloud, is a global network of servers hosted in state-of-the-art facilities managed exclusively by ISL Online in accordance with strict security standards.
ISL Online Cloud is a secure and dependable platform for hosting remote desktop sessions. It provides users with a high-availability infrastructure, and its servers are located in multiple secure data centers across the globe. This enables users to connect to the network from any location, with fast and stable connectivity and minimal latency.
Getting Started
Session
A session refers to a remote desktop connection initiated by a user using ISL Light.
There are two types of sessions:
Remote Support Session or Attended Sessions
Remote support sessions using ISL Light typically start with the technician initiating the session by starting ISL Light and generating a unique session code or link. This session code or link is then shared with the customer, who enters it into their ISL Light Client software on their computer to join the remote support session.
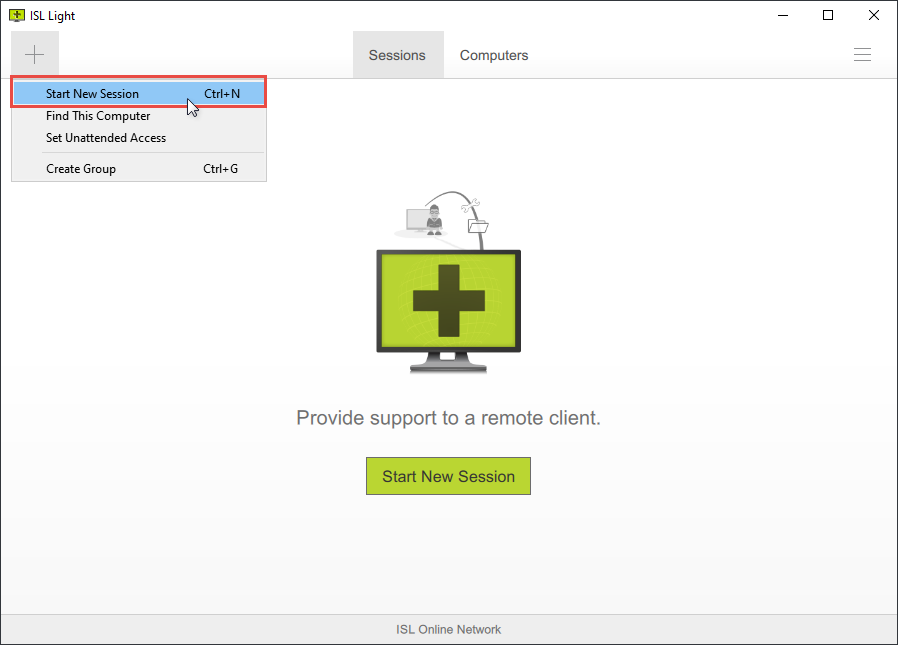
ISL Light > Sessions > Connect with Client
Remote Access Session or Unattended Sessions
Remote access sessions, on the other hand, are initiated from ISL Light and involve installing ISL AlwaysOn, a remote agent, on the remote computer. Once installed, the remote agent allows 24/7 access to the remote computer, enabling the technician to remotely access and control the device as needed, without requiring the presence or intervention of the remote user.
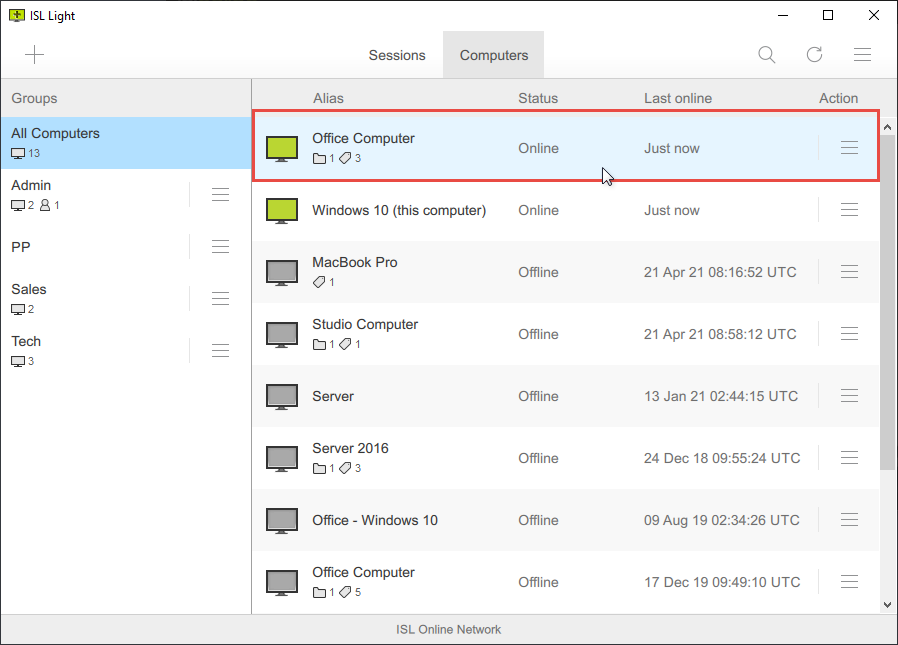
ISL Light > Computers > Connect to Remote Computer
In summary, ISL Online sessions are started from ISL Light and can either be remote support sessions, which require a unique session code or link and involve the customer running ISL Light Client, or remote access sessions, which require the installation of ISL AlwaysOn on the remote computer and provide 24/7 access to the device.
Code
Session Code
A session code or link is a unique code or link generated by the ISL Light software every time a new session is started. It is used to connect two endpoints, such as a support technician and a customer, in a remote support session.
The session code or link is typically shared via email, chat, or other messaging services. The code can be entered into the ISL Light Client software or at www.islonline.net by the customer to establish the connection.
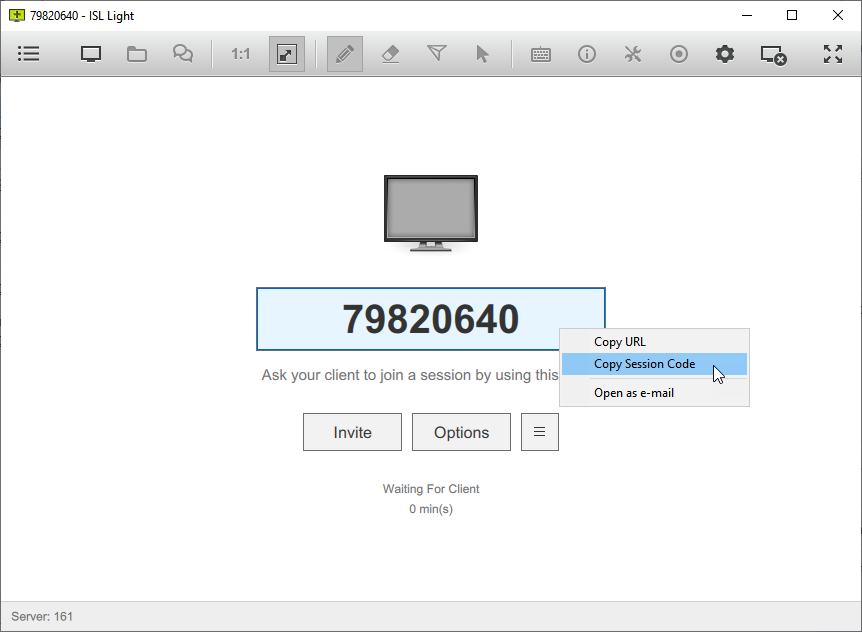
ISL Light > Sessions > Start New Session
Grant Access Code
A grant access code or link is a permanent code or link generated based on a computer group that allows the operator to download and install ISL AlwaysOn, the remote access agent, on a remote computer. This code or link can be shared with the operator to give them access to the computer at any time.
The grant access code or link is typically shared via email, chat, or other messaging services and must be entered into a web browser by the operator to download and install ISL AlwaysOn on the remote computer. Once installed, ISL AlwaysOn allows the operator to remotely access and control the computer as needed, without requiring the presence or intervention of the remote user.
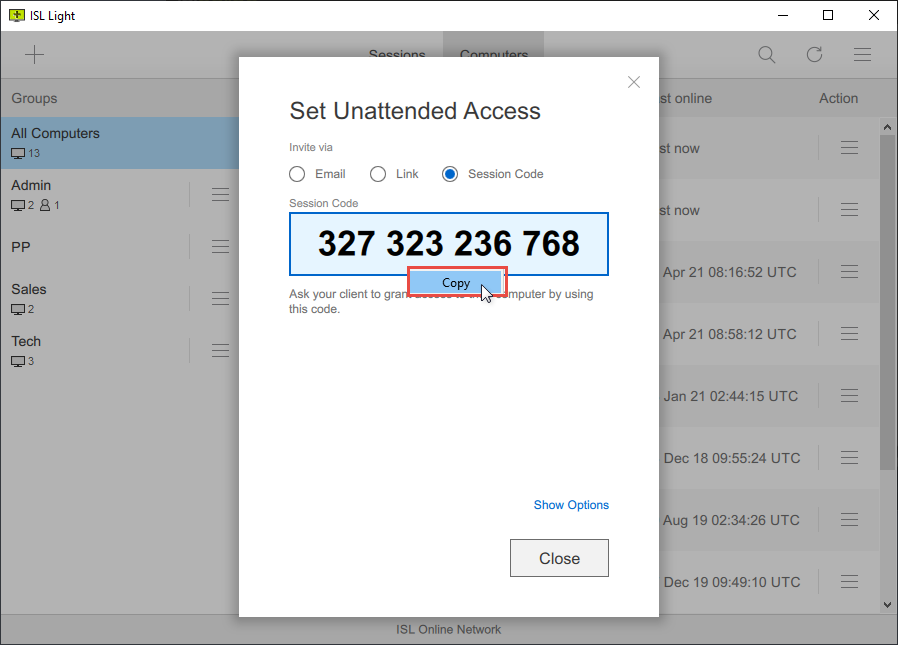
ISL Light > Set Unattended Access > Code
Passwords
Account Password
An account password is the password used by a user to log in to their ISL Online Account. The account password is set during the account creation process and can be changed at any time by the user from their account settings.
Choosing a strong and unique password is highly recommended to protect the ISL Online Account from unauthorized access. A strong password typically includes a combination of uppercase and lowercase letters, numbers, and special characters. It is also important to avoid using easily guessable information such as birthdates, names, or common words in the password.
ISL Online also provides additional security measures such as two-factor authentication, which requires the user to provide a second form of authentication in addition to the account password to access the account. This additional security measure helps to prevent unauthorized access to the account even if the account password is compromised.
Access Password
An access password is a security feature used to protect remote connections to a computer. When connecting to the remote computer, the user will be prompted to enter the access password.
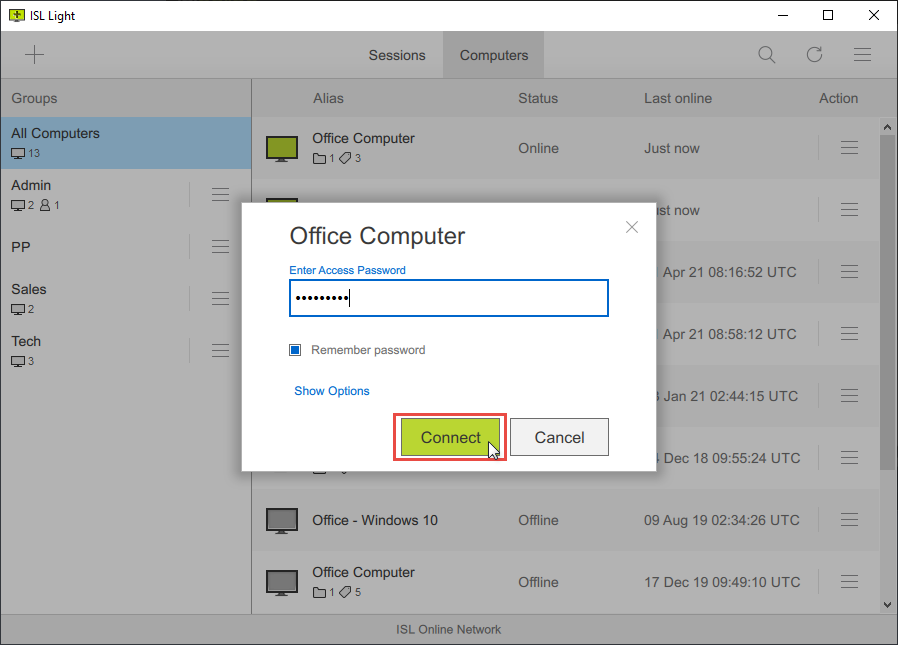
ISL Light > Computers > Type Access Password
Main Access Password
To restrict remote access to a computer to authorized users only, it is necessary to set a main access password on the first installation of a remote access agent (ISL AlwaysOn). This password serves as a security measure to prevent unauthorized access to the computer.
It's important to note that if you forget your Main Access Password, it can only be reset on the remote computer through ISL AlwaysOn.
Connection Access Password
The connection access password is an optional password that can be manually set in the ISL Light per computer or in ISL AlwaysOn settings. This password adds an extra layer of security when sharing a computer with multiple users or user groups.
One-Time Password(s)
One-time passwords are a set of unique passwords generated within the ISL AlwaysOn settings.
Features
For a comprehensive list of all features available with our products, please refer to our features table. This table is an essential resource for understanding the capabilities of our product and can help you determine if it's the right fit for your needs.
Administration
"Administration" in ISL Online refers to the management of various features and options at both the domain level and individual user level. Administrators have access to a range of tools and settings that allow them to manage and oversee all aspects of the software, including all computer groups, domain and user permissions, user groups, and more. With the Administration menu, administrators can easily assign permissions to users, audit administration actions, and customize settings to meet the needs of their organization.
ISL Online web console > Administration
Administrative Mode
"Administrative Mode" is a feature in ISL Light that enables the operator to interact with the Windows User Account Control on a remote computer and perform administrative tasks that require elevated permissions. Once Administrative Mode is enabled, the operator can access additional functionalities such as restarting the remote computer and having the ISL Light session resume upon startup.
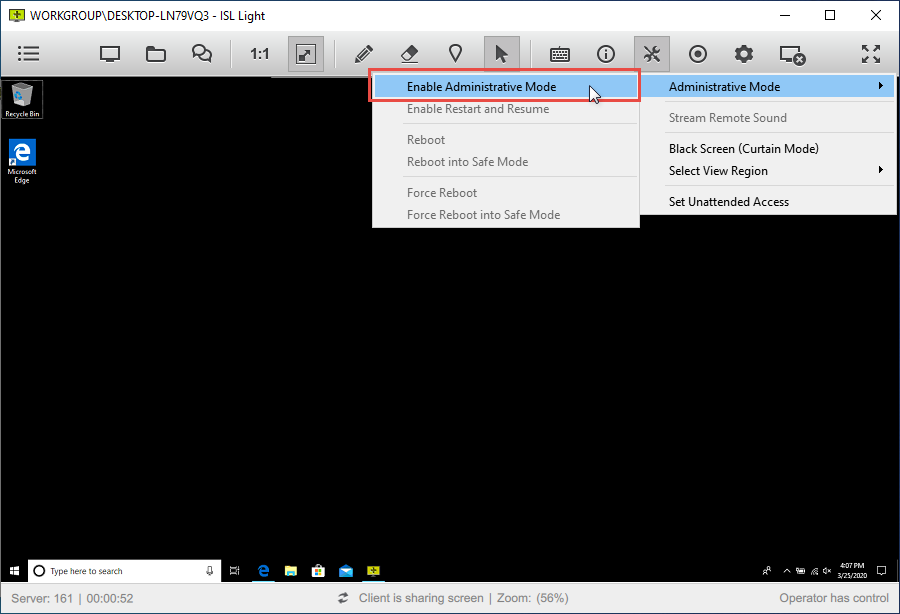
ISL Light > In Session > Administrative Mode
License Usage
"License usage" refers to the web page that displays all active sessions currently in use. If the concurrent session limit is reached for your account, you will be prompted to visit this page to terminate an ongoing session and free a license.
Firewall Ports
Firewalls are network security systems designed to filter network traffic based on trusted and untrusted sources. They apply preset or dynamically learned rules that allow or deny connection attempts, securing private networks and their corresponding endpoints called network hosts.
ISL Online products use specific ports for communication. The default ports used by ISL Online for standard connections are TCP 80, 443, and 7615. Port 7615 is the preferred choice and is considered the default port for ISL Online, similar to how SSH uses port 22, TELNET uses port 23, SMTP uses port 25, and RDP uses port 3389.
When direct connection is available, connections require UDP/TCP ports used by STUN/TURN servers and arbitrary high ports for relay connections. Firewalls can filter traffic based on protocols, IP addresses, and ports used, so it is important to ensure that the necessary ports are open for the ISL Online products to work properly.
Two-Factor Authentication (2FA)
Two-Factor Authentication (2FA) is an additional security measure for ISL Online users. When 2FA is enabled, users must go through a two-step verification process to log into the system, providing something they know (a password) and something they have (a 2FA token).
It is recommended to set up multiple 2FA methods, such as mobile and email, to ensure backup options are available in case of lost or compromised authentication methods. With 2FA enabled, ISL Online ensures a higher level of security for its users and their data.
External Authentication
External authentication is a method of user authentication in which an external system or service is used to verify the identity of a user attempting to access a system or application. Instead of using a username and password that is managed by the system or application itself, external authentication relies on the user's credentials being verified by a third-party system such as an LDAP server, Active Directory, NetIQ eDirectory, RADIUS, SAML 2.0 or OAuth provider. By using external authentication, users can use the same credentials they use for other systems or applications, which can improve security and simplify the login process.
Access Filters
Access Filters in ISL Online are a security feature that allows administrators to control and restrict remote access based on IP and/or MAC addresses. These filters are a set of rules that permit or deny access to specific resources in the system based on the source address of the incoming connection. Access Filters can be configured at the domain or user level through the Administration pages, or per computer by setting access filters in ISL AlwaysOn. This provides an additional layer of protection against unauthorized access or misuse.
RDP, VPN and ISL Light
Remote Desktop Protocol (RDP) and Virtual Private Network (VPN) are two distinct technologies used for remote access to computers or networks. RDP is a proprietary protocol developed by Microsoft, allowing a connection to a PC running on the same local area network (LAN). A direct peer-to-peer connection to the remote PC via LAN is required for an RDP connection, but if the PC is located outside the LAN, a VPN connection must be established or port forwarding configured on the router/firewall. However, ISL Online enables establishing an RDP connection to a Windows computer in a remote network without VPN tunneling or any firewall changes.
On the other hand, a VPN creates a secure and encrypted connection between a remote device and a private network. It is commonly used to access company resources remotely or protect internet traffic while using public Wi-Fi networks. When a user connects to a VPN, they are effectively connected to the network as if they were physically present in the office.
While both RDP and VPN serve different purposes, they can be used for remote access. RDP is primarily used for accessing specific computers or servers remotely, while VPN is used for accessing entire networks or resources. One of the main advantages of using ISL Light over RDP or VPN is that it allows an RDP connection to be established to a Windows computer in a remote network without VPN tunneling or any firewall changes, providing a high level of security without requiring additional hardware or software. Additionally, ISL Light offers a range of features and tools designed to improve the remote desktop experience, such as real-time file sharing and collaboration.
If an RDP session is preferred, ISL Online can open a session with RDP or connect to an existing RDP session without requiring a VPN or firewall changes by creating a tunnel itself (Remote Desktop Tunneling). Thus, the traffic security is not compromised and is additionally protected by the 256-bit encryption of AES. For more details, please refer to the Connect via RDP/SSH article.
Secure Shell Protocol (SSH)
Secure Shell (SSH) is a cryptographic network protocol used for secure communication over an unsecured network. It provides strong encryption, authentication, and integrity protections to ensure that sensitive data and communications are protected from interception or manipulation by unauthorized users. In the context of ISL Light, SSH is used as an alternative to RDP for remote desktop connections. ISL Light enables users to establish an SSH connection through terminal to a remote computer, which can be especially useful in Linux environments where RDP is not available or where the user prefers a command-line interface.
To review legal terms for our services, please refer to our License Agreement.