Dicas de Segurança
Entendemos que a segurança das informações é de extrema importância. Seguimos padrões industriais de segurança para proteger seus dados.
Para estabelecer uma conexão de suporte remoto com um cliente, o operador de suporte precisa iniciar o aplicativo ISL Light, que contém uma Chave Pública RSA de 2048/4096 bits do servidor da ISL Online. A ISL Online garante a segurança de sua conexão remota padrão usando criptografia AES de 256 bits de ponta a ponta. Servidores STUN/TURN possibilitam uma conexão direta, enquanto o canal de sinalização e controle permanece nos servidores da ISL Online. Nestes casos, o ECDSA P-256 gerencia a negociação da chave de criptografia usando o algoritmo de troca de chaves Diffie-Hellman, garantindo a conexão usando criptografia AES de 256 bits de ponta a ponta.
O software suporta autenticação de dois fatores, logs de auditorias exportáveis, gravação de sessão automática e autenticação externa.
Para mais detalhes leia nosso declaração de segurança.
Abaixo está um resumo dos recursos importantes que o ISL Online fornece para garantir uma utilização segura do software de desktop remoto.
Login
Quando você loga em sua conta ou ISL Light, recomendamos que utilize uma senha forte e configure a autenticação de dois fatores para tornar sua conta mais segura.
Utilize senha de acesso forte
A segurança de seus dados depende não apenas da criptografia, mas também de sua senha.
Para ajudar você a criar uma senha forte, a política de segurança de senha da ISL Online é baseada nas últimas especificações do NIST. Sua senha deve ter pelo menos 8 caracteres de comprimento. Você pode usar qualquer caractere ASCII imprimível e espaços, enquanto quaisquer espaços iniciais e finais serão removidos. Sua senha é verificada em relação à lista de negação, que consiste nas senhas mais comuns e simples.
Ajuste autenticação de 2 fatores
A autenticação de dois fatores é a camada extra de segurança. Para logarem, os técnicos precisarão passar por esse processo.
Como configurar autenticação de dois fatores
Importante:Recomendamos criar mais de um método de autenticação de dois fatores, como celular e e-mail. Isso te dá mais opções para o login caso você perca seu acesso.
Autenticação Externa (Licença Servidor)
Vários tipos de esquemas de autenticação podem ser integrados como OpenLDAP, Microsoft Active Directory, Novell eDirectory, ou RADIUS. Quando a autenticação externa é configurada, os direitos de acesso do operador e permissões para utilizar o software ISL Online são gerenciados pelos administradores de TI utilizando seus diretórios de gerenciamento.
Senha de Acesso
Quando você instala acesso isolado (ISL AlwaysOn) em um computador remoto, você precisa criar uma senha de acesso segura. Essa será sua principal senha de acesso, que você precisa fornecer cada vez que acessa o computador remoto.
Senha de acesso principal
Principal senha de acesso que é definida durante a instalação, e pode ser utilizada para conectar com o computador remoto por qualquer usuário.
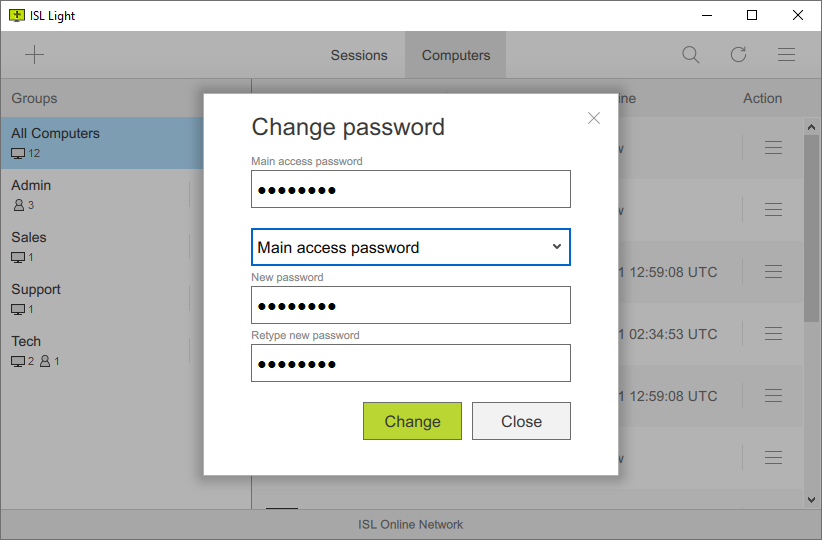
Senha de acesso a conexão
Você pode criar senhas diferentes para usuários com quem já tiver compartilhado acesso. Elas podem ser criadas manualmente nos ajustes do ISL AlwaysOn.
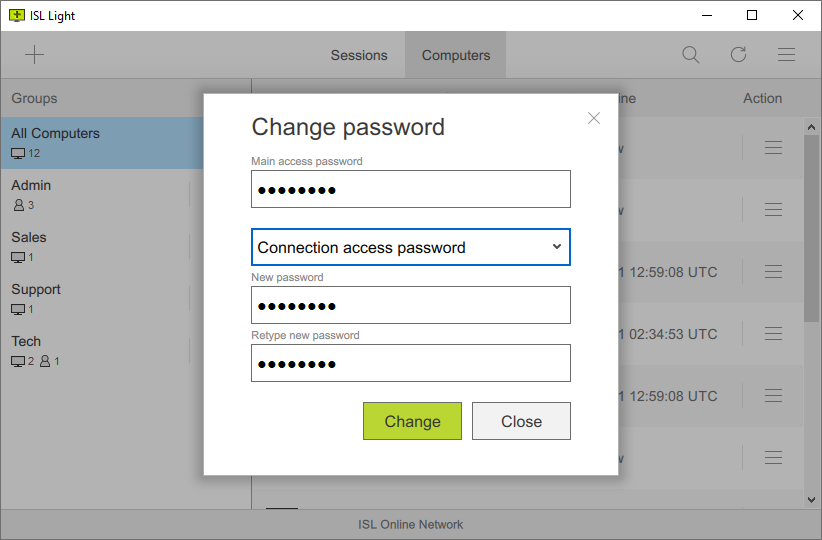
Senha de Acesso Único
Gere senhas únicas manualmente nos ajustes do ISL AlwaysOn. Elas podem ser usada uma única vez.
Ler manual Assista o vídeo (3:14)
Configurações Adicionais
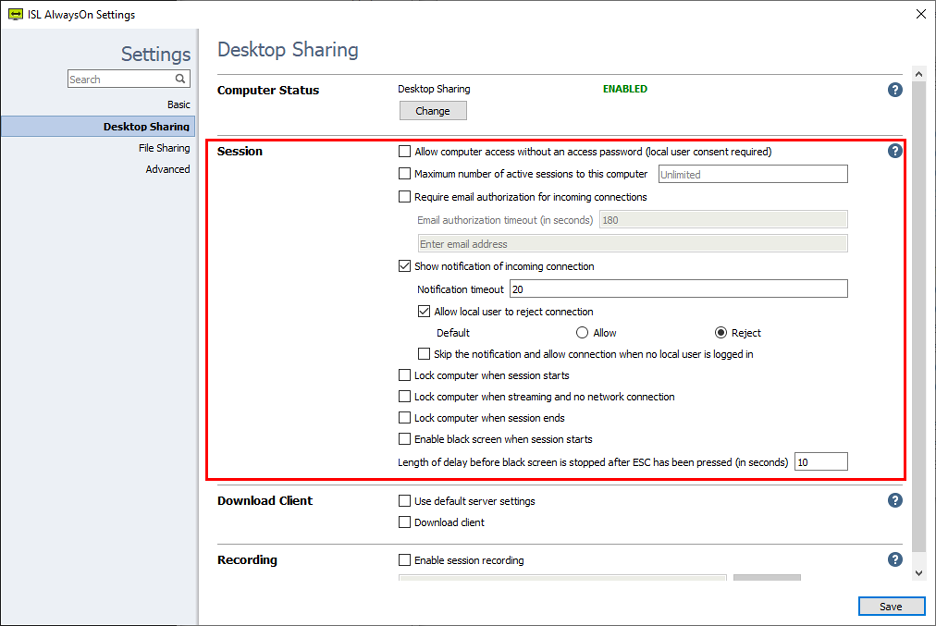
Os ajustes do ISL AlwaysOn permitem que você modifique ou personalize vários ajustes de segurança para se conectar a um computador isolado.
Permitir acesso ao computador também com autorização do usuário local e nenhuma senha de acesso.
Permite que o operador se conecte a um computador remoto sem uma senha de acesso. Nesse caso, o usuário local deve aprovar a conexão. Para usar essa configuração, você deve usar os seguintes parâmetros de linha de comando ao iniciar o ISL Light:
ISLLight.exe --username "<isl_online_username>" --password "<password>" --connect-search "<computer_description>/<computer_name>" --consent-message "<message to be displayed>"
Número máximo de sessões ativas para esse computador
Permite definir o número máximo de sessões ativas para este computador. Por exemplo, para limitar o acesso a uma conexão simultânea ao computador, use o valor '1'. O padrão é definido como Ilimitado.
Exibir noticações de conexões em andamento
Permite que seu cliente veja uma contagem regressiva quando a conexão com seu computador é estabelecida. Você pode ajustar o tempo e as opções que estarão disponíveis para o usuário local. Depois do tempo, a ação padrão é executada se o usuário remoto tiver permissão para cortar a conexão.
Permitir usuário local rejeitar a conexão
Essa opção fica disponível se você habilitar a opção "Exibir notificação da conexão de entrada". O usuário local vê a notificação que dá a eles a opção de aceitar ou negar a conexão.
Bloquear o computador quando iniciar a sessão
Bloqueie o computador remoto no início da sessão, você precisará inserir os dados da conta para entrar.
Bloquar computador quando estiver transmitindo e sem conexão de rede
Se a conexão for interrompida, o computador remoto é bloqueado automaticamente.
Bloquear computador ao final da sessão
Bloquear o computador automaticamente ao final da sessão.
Habilitar tela preta quando iniciar a sessão
O usuário local verá uma tela preta quando a sessão remota estiver ativa.
Tempo antes da tela preta ser parada após pressionar a tecla ESC (em segundos)
Ajuste o tempo em segundos para iniciar com a tecla ESC. Quando o tempo termina, a tela preta é desabilitada e o cliente local pode ver a tela. O tempo máximo é de 180 segundos.
Notificações por e-mail
Receba uma notificação por e-mail cada vez que a sessão de acesso remoto iniciar, parar, falhar ou quando um arquivo for baixado por um computador específico.
Ler manual Assista o vídeo (0:58)
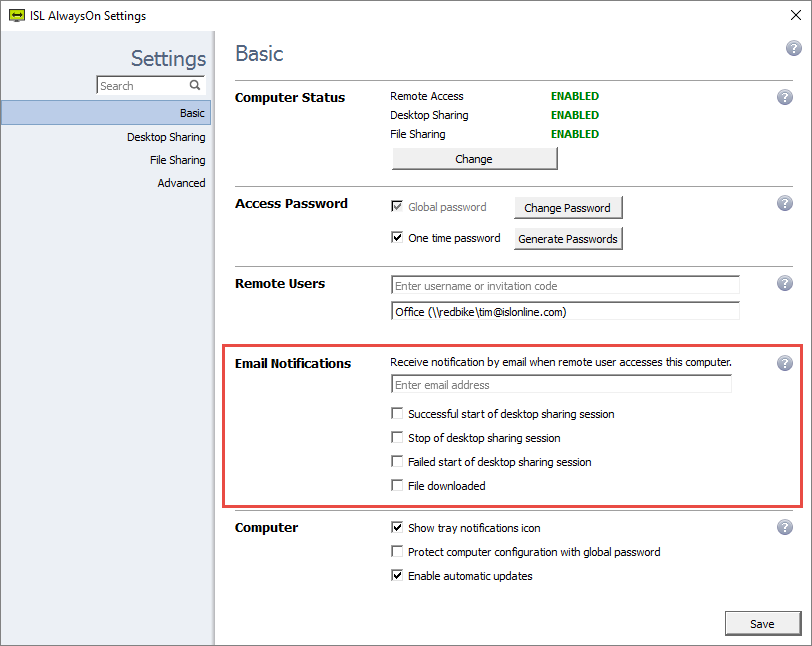
Filtros de Acesso
Por questões de segurança você pode restringir a utilização do software ISL Online aos limites de sua empresa. Você pode restringir o limite de acesso a dados aos servidores ISL Online baseado nos endereços IP e MAC. Utilize a função "permitir" para especificar a lista de endereços IP e MAC que têm permissão para iniciar uma sessão de suporte remoto ou acessar um computador isolado. Por outro lado, você pode utilizar a função "negar" para especificar a lista de IP e MAC não permitidos. Essas regras podem ser definidas para um usuário específico ou o domínio inteiro no servidor ISL Online.
Por exemplo, você pode permitir que seus empregados gerem códigos de acesso apenas do escritório (nos limites do seu endereço de IP).
- deny_ip 192.168.0.14
- allow_ip 192.168.0.13/255.255.255.0
- allow_mac 00-19-d1-06-c9
Os endereços IP e MAC podem ser descobertos, portanto os filtros apenas não substituem uma senha de acesso forte!
Ler manual Assista o vídeo (0:56)
Filtragem de Port
Um bom software de desktop remoto funciona sem a necessidade de ajustes no firewall.
Com a ISL Online, seu firewall pode permanecer intacto, pois o ISL Light inicia automaticamente uma conexão de saída, tentando se conectar usando as portas 7615, 80 ou 443.
No entanto, organizações maiores podem ter uma política estabelecida em relação à configuração de seus firewalls ou proxies. Os administradores de sistema podem querer abrir a porta 7615 apenas para permitir o tráfego da ISL Online passar diretamente e continuar filtrando o restante. Eles também podem configurar exceções de nome de DNS ou exceção de endereço IP.
Independentemente da configuração de rede, os aplicativos da ISL Online automaticamente tentarão diferentes abordagens para encontrar um transporte de trabalho (detectando configurações de proxy, usando WinINet, criando um túnel, fazendo uso do DNS wildcard etc.). Quando uma Conexão Direta é usada, o firewall deve permitir a conexão através das portas necessárias para os protocolos STUN e TURN. Mais comumente, a porta 3478 é usada, no entanto, as conexões de retransmissão são feitas em portas altas arbitrariamente selecionadas.
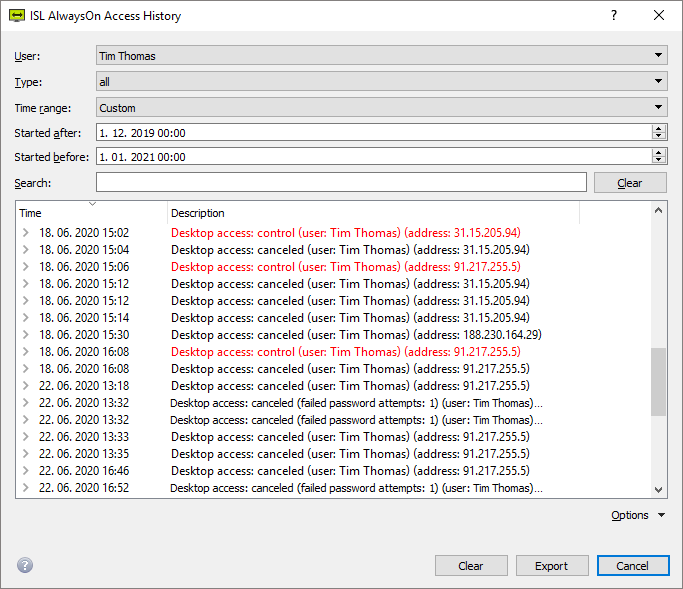
Histórico de Acesso do Computador
Buscar conexões que tenham sido estabelecidas em sua conta, marcadores de horários de conexão do desktop, e outras informações uteis.
Ler manual Assista o vídeo (0:34)
Restrição de Recursos
O software de desktop remoto é uma ferramenta universal, utilizado virtualmente em todas as industrias. Existem diferente situações em que soluções flexíveis com a possibilidade de restrições de funções para aderir a padrões de segurança distintos.
O ISL Online te permite restringir recursos que estão disponíveis em uma sessão: controlar o computador remoto, transferência de arquivos entre cliente e operador e muitos outros recursos.
Um exemplo de onde essa restrição é essencial: o funcionário de um banco pode visualizar a tela de um cliente, mas nunca compartilhar seu próprio desktop. Nesse caso, o compartilhamento de tela do lado do atendimento pode ser desabilitado.
Opção Intranet (LAN-apenas)
Algumas grandes empresas utilizam o ISL Online apenas para suporte interno. nesses casos, o software de desktop remoto deve permitir sessões de desktop remoto na rede (LAN) local apenas.
Se você pensa em utilizar o ISL Online apenas em seu LAN (intranet), não há necessidade de um IP público. Você precisa apenas de um endereço privado no alcance de redes privadas (como especificado no RFC 1918).
Principais Perguntas
-
Quais ports precisam ser abertos para soluções hospedadas?
O port 7615 é o preferido e você pode considerá-lo o port padrão ISL Online, assim como o 22 é ssh, 23 telnet, 25 smtp, 3389 rdp etc. - você também encontra em lista de ports na wikipedia.
Ter um port específico é muito conveniente. Se necessário, abra o port 7615 e todos os produtos ISL Online funcionarão perfeitamente. Com os 80/443, o admin acharia difícil tentar permitir o ISL Online, mas limitar o tráfego que também passa por lá.
Em geral, a primeira coisa a considerar é verificar se é possível fazer uma exceção. Isso não significa desabilitar o proxy completamente, apenas permitir o tráfego ISL Online e filtrar o resto. Se exceções de nomes DNS forem permitidas, libere tcp direto do port 7615 para *.islonline.net. Se o proxy apenas permitir exceções de números de IPverifique esse link para a lista atual de nossos IPs de servidores. Conexões diretas oferecem melhor performance e atrasos mínimos.
Num mundo de conexões diretas ideais e políticas de segurança flexíveis, a história terminaria aqui, mas já que há muitos clientes atrás de firewalls/proxies onde apenas tráfego http é permitido (portanto, port 80 e, ou 443) e os administradores de sistema e rede não querem ou não podem fazer exceções, também damos suporte e nossos apps buscam um caminho nessas situações (detectar ajustes proxy, utilizar wininet, criar um túnel, utilizar o cartão dns - ajuda com proxies, etc.).
Situações com a necessidade de filtragem podem sofrer maiores atrasos, principalmente por transporte na conexão. Os produtos ISL Online sempre tentam conexão direta utilizando o port 7615 e, caso falhe, tentam os ports 80 e 443 com vários métodos proxy. Cada tipo de transporte dura 7 segundos e no windows tentamos 8 tipos de transportes, portanto se o último funciona, isso representa um atraso de quase 1 minuto. Se um cliente reclamar de longos atrasos, o melhor a fazer é se conectar ao computador problemático e clicar em encontrar melhor transporte. Você verá uma lista de transportes bem sucedidos junto a uma taxa média de transferência, atrasos, etc. Esses resultados permitirão forçar o melhor transporte. Tanto você quanto seu cliente apreciarão o atraso de conexão reduzido.
Entre em contato com ISL Online por telefone, e-mail ou chat ao vivo se precisar de ajuda.
-
Quanto tempo a sessão ISL Light fica registrada no sistema?
Uma sessão está ativa quando o ISL Light está ativo. Quando o ISL Light é fechado ou apenas a sessão é fechada, a sessão não está mais ativa. O sistema continua com suas informações básicas (os números IP do ISL Light e Cliente, transcrição do chat. quantidade de dados transferidos, etc.) A sessão pode também ser encerrada de forma automática após tempo pré-determinado. O tempo conta a partir da última utilização do computador.
-
Como configuro meu firewall?
Se não filtrar conexões, nenhuma alteração é necessária. No entanto, se você filtrar, liste todas as conexões para *.islonline.net.
-
Como devo configurar meu firewall para obter a melhor experiência com a ISL Online se ele não suportar a lista de permissões de DNS? Quais endereços IP devo permitir?
Veja a lista de servidores para uma lista atualizada de endereços IP. No entanto, lembre-se que a lista muda com o tempo. Um proxy ISL Online pode ser configurado para minimizar a lista de regras e reduzir a manutenção a quase zero. Para mais informações, veja manual.
-
Seu ISL Light é seguro contra hackers?
O ISL Light utiliza criptografia SSL/TLS padrão industrial. Você pode ter certeza de que sua sessão estará segura - criptografada de ponta a ponta - do ISL Light Client para o ISL Light. O cliente precisa permitir cada ação para que o operador não assuma o controle do computador. Não é necessária nenhuma alteração no Sistema Operacional. Para maiores informações, favor ir para segurança.
-
A sessão continua se meu IP local mudar no meio de uma sessão?
Sim, o ISL Light se reconecta ao servidor, quase como se desplugasse e plugasse um cabo de volta.
Continuar Lendo: Mais Sobre Segurança